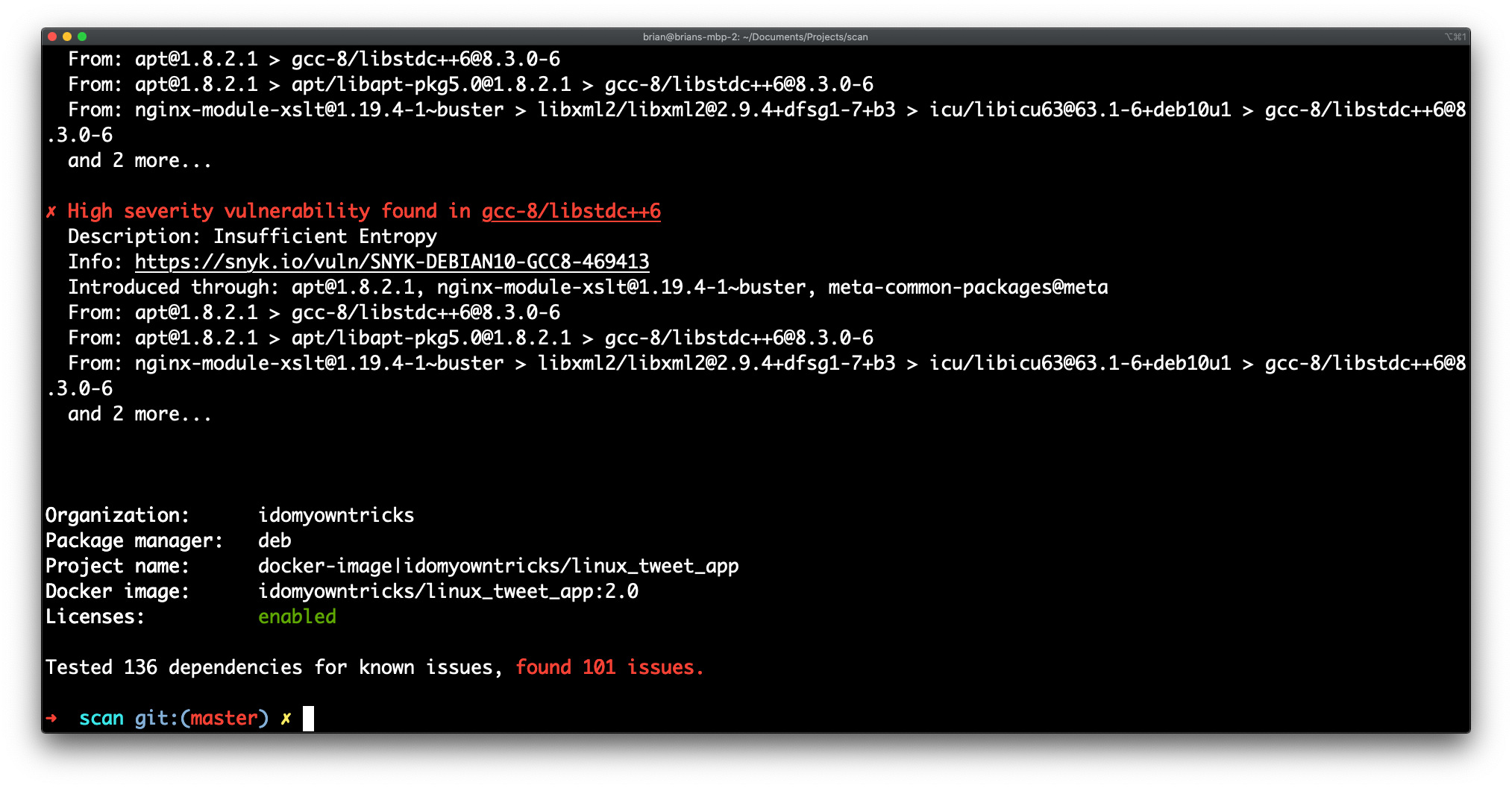
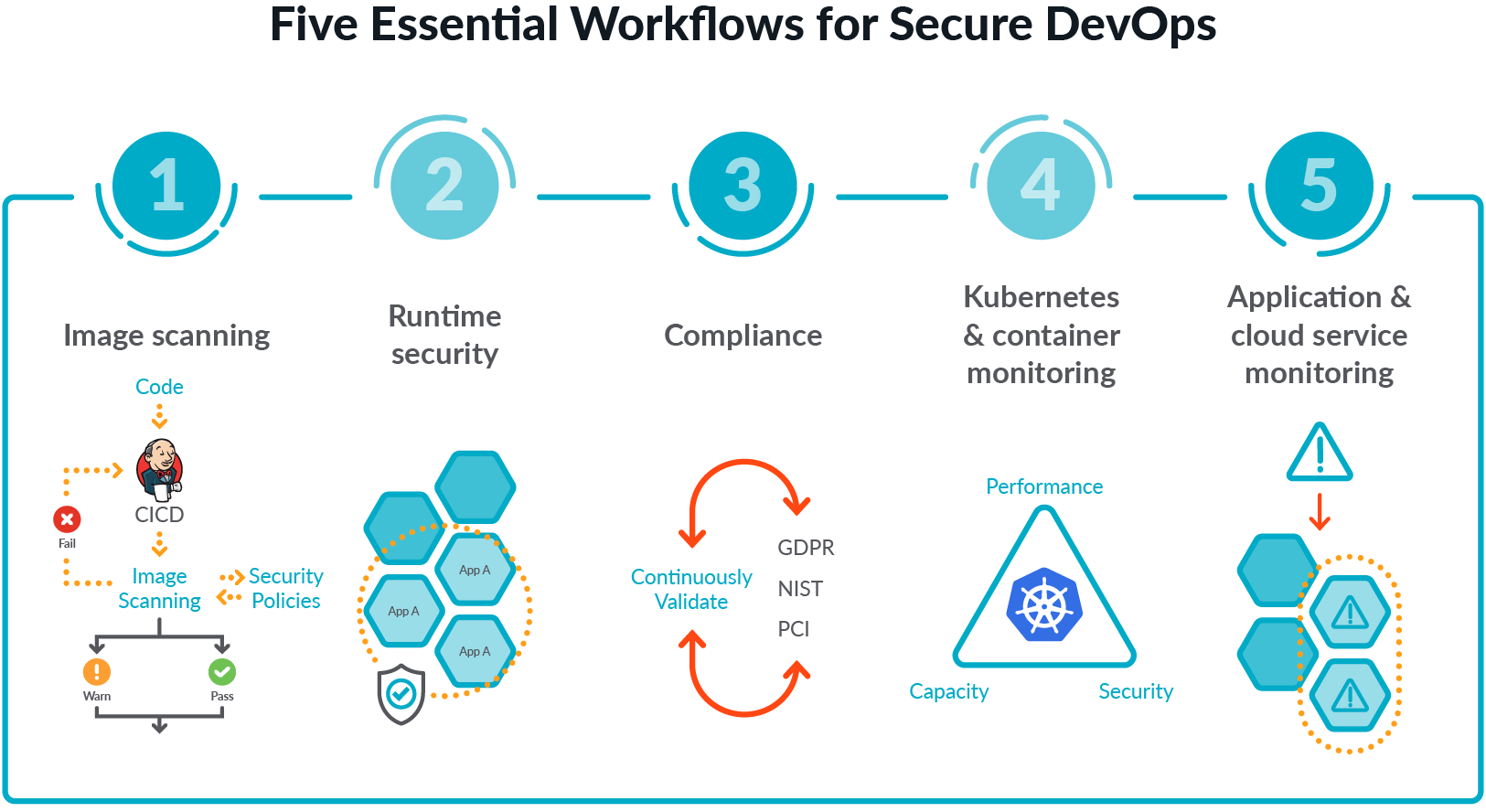
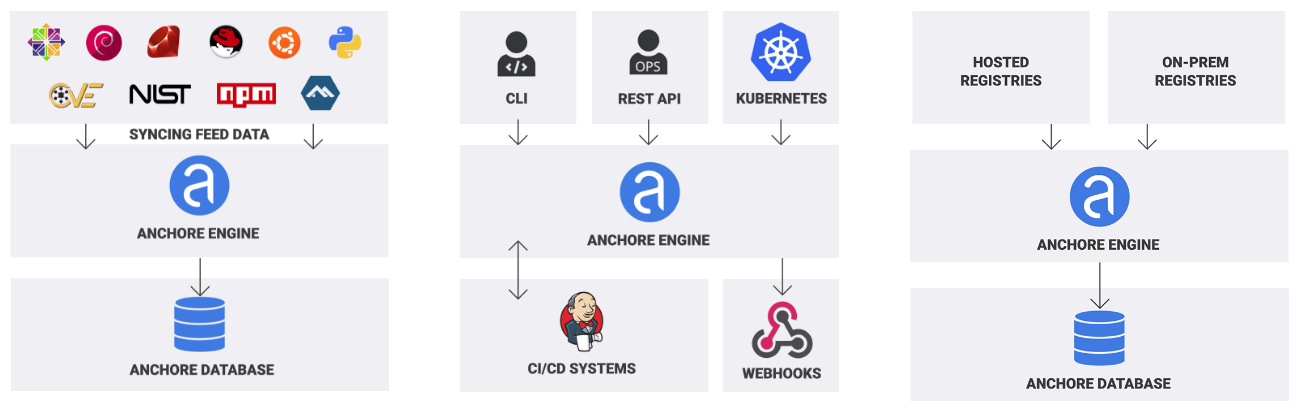
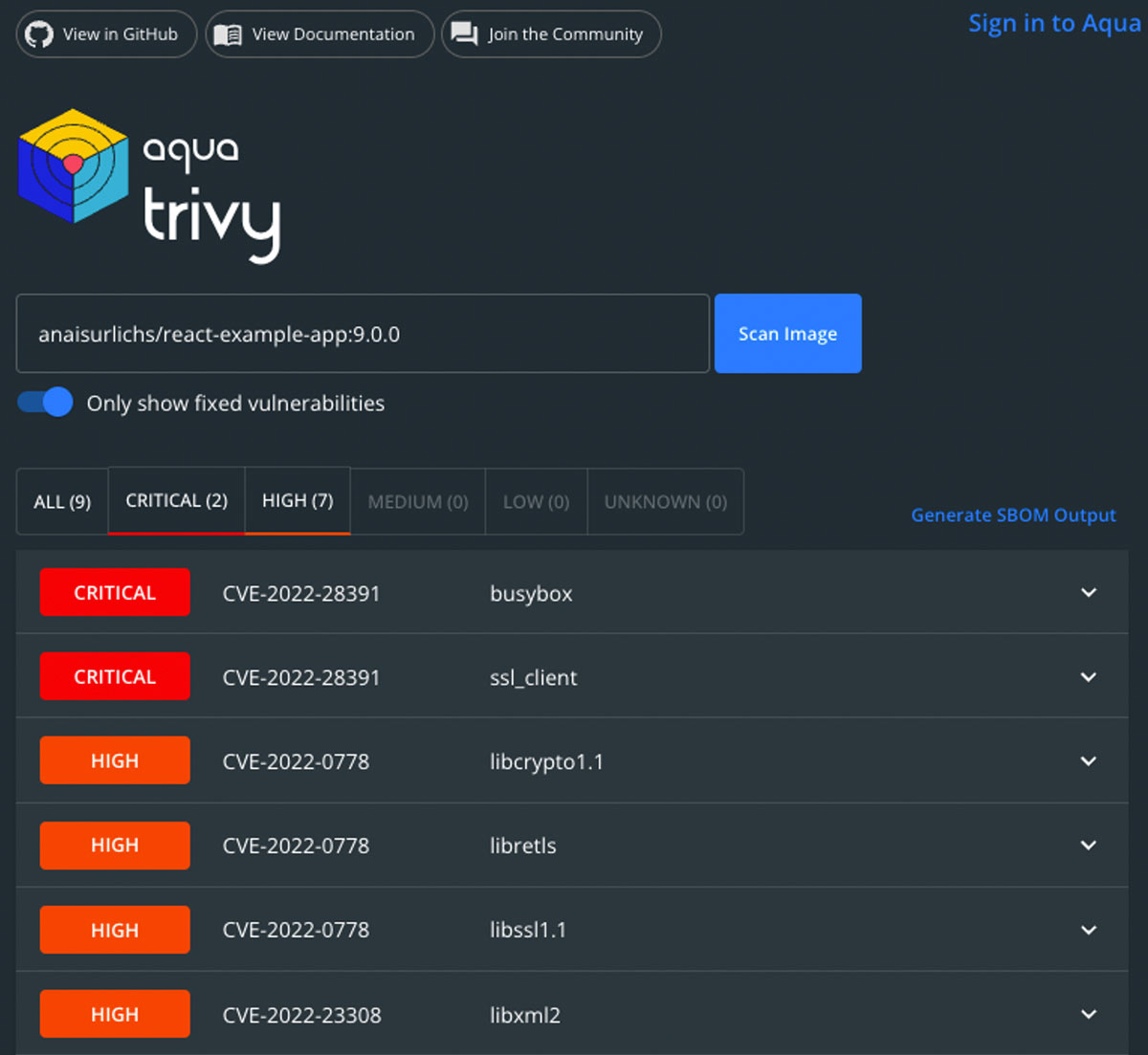
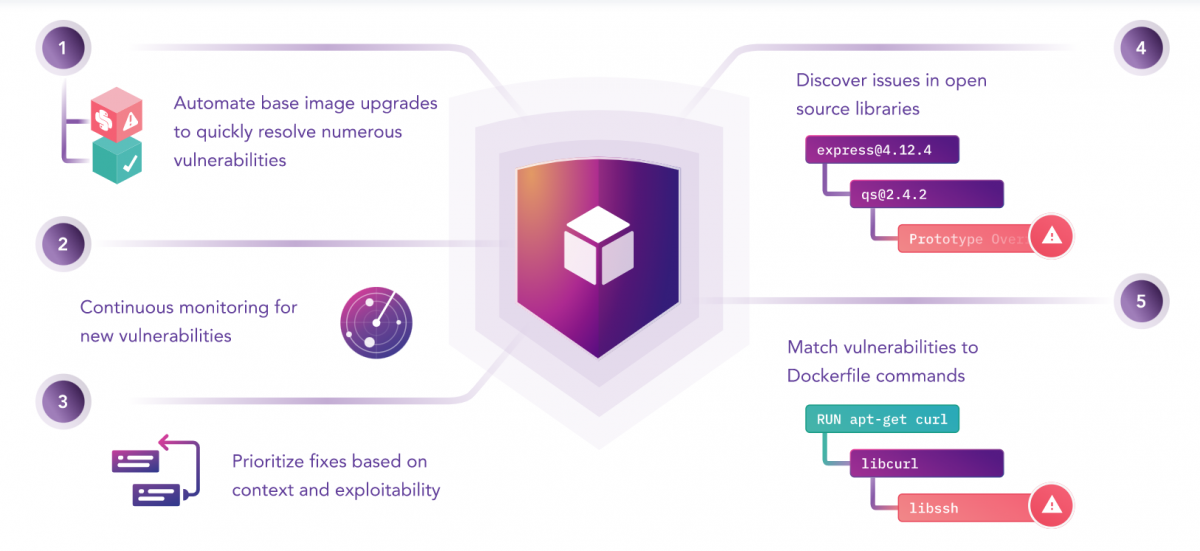
How to Scan Docker Image for Vulnerabilities with Snyk? | How to Fix Docker Image Vulnerabilities? - YouTube

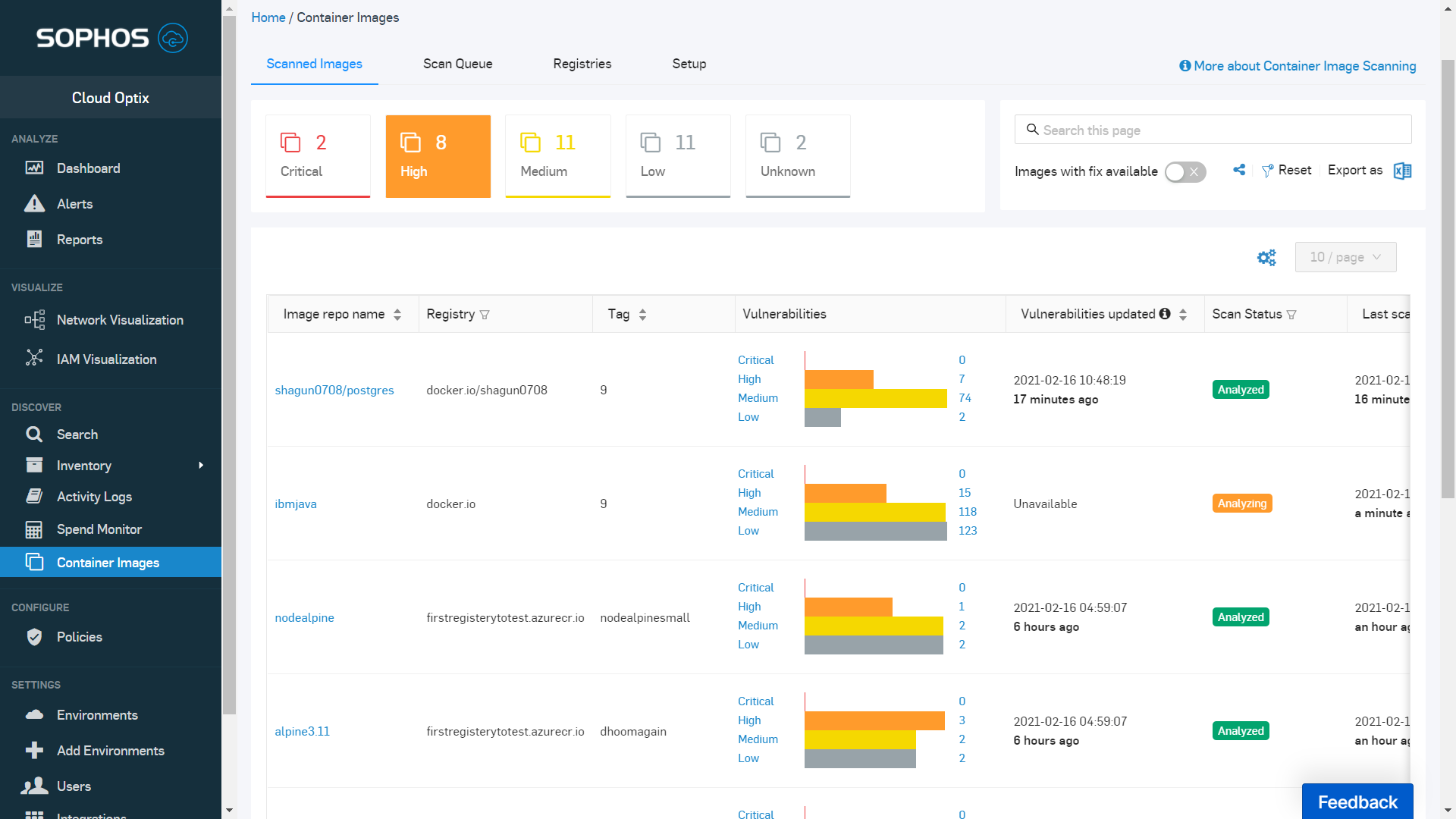
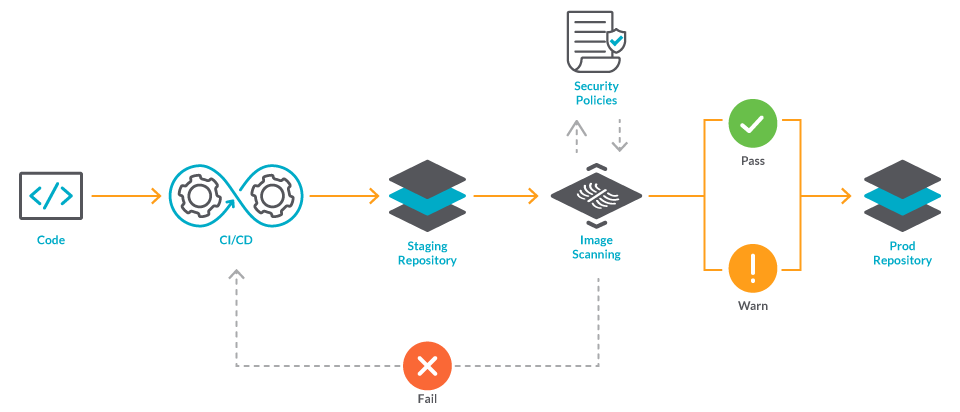
Introducing Container Image Scanning: Identify both misconfigurations and vulnerabilities with Bridgecrew

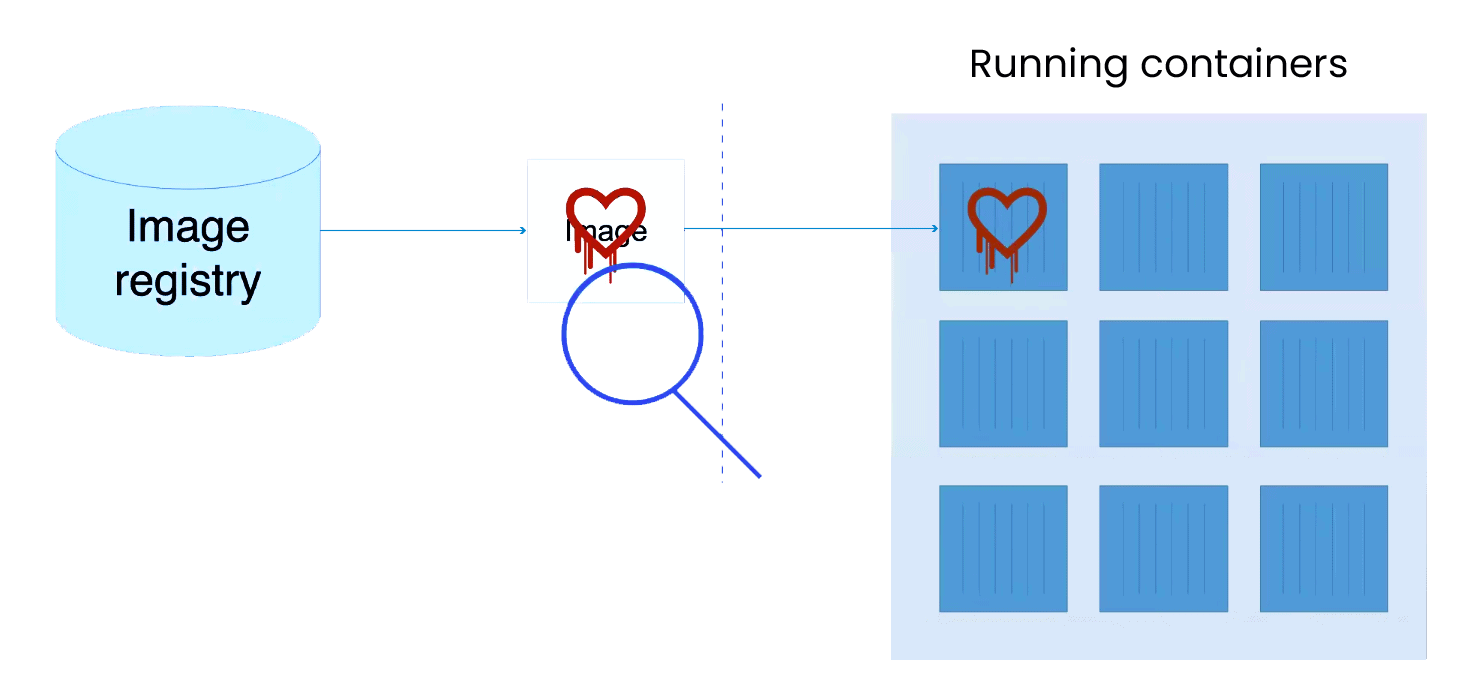
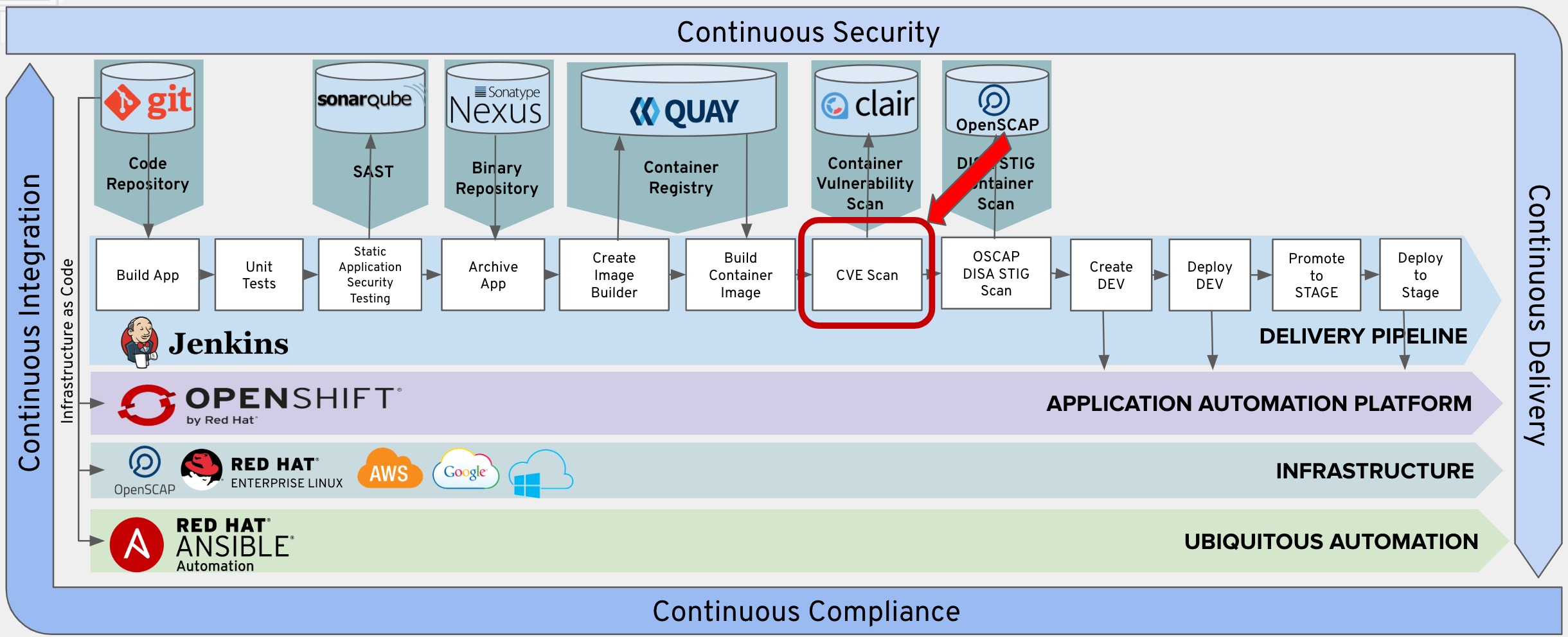
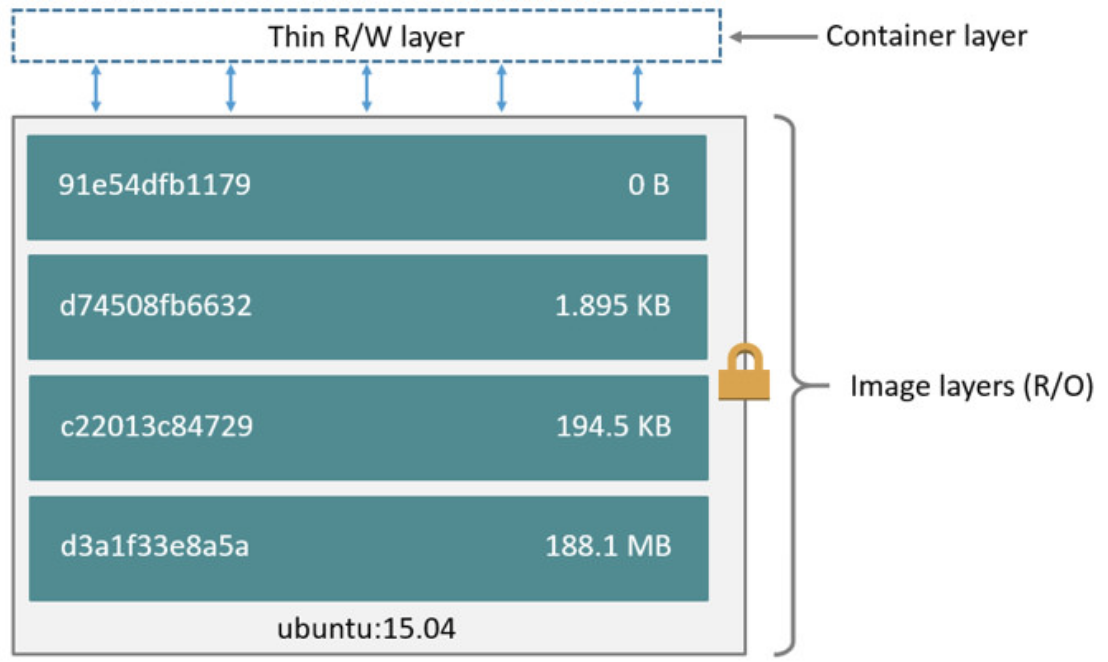
Scanning Docker Images for Vulnerabilities using Clair, Amazon ECS, ECR, and AWS CodePipeline | AWS Compute Blog